Microsoft’s cloud ecosystem boasts a robust and multifaceted approach to service-to-service communication security. This intricate landscape, familiar to developers familiar with Azure AD (now evolved into Entra ID), reflects Microsoft’s long-standing commitment to robust identity and access management solutions. At the heart of this layered approach lies the fundamental principle of the Three A’s: Authentication, Authorization, and Audit. This article delves specifically into the realm of Authentication, focusing on Managed Service Identities as a cornerstone for establishing secure communication between Azure services.
Basic Authentication Link to heading
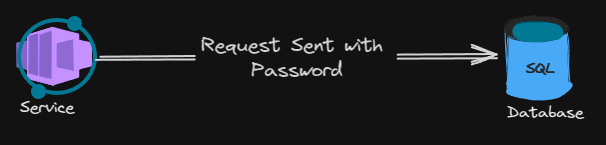
Basic authentication is the oldest form of authentication, in short there is a password or passphrase (a secret) often paired with a username, these are sent with each request to a service as proof that the service can trust the client. This method of authentication is very simple to implement as it only requires 2 parties (a client and a Server) and can be as simple as sharing a single key.
Basic authentication is not without its risks, as the password is sent with every request if the request is intercepted then the password has been compromised, in my experiences passwords are not frequently rotated meaning that if the password is compromised it may be used by the compromising party until the password is rotated.
Token Based Authentication Link to heading
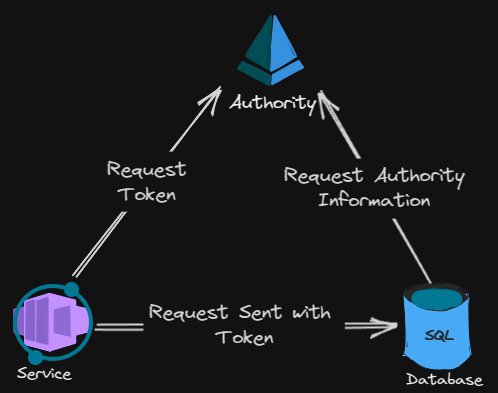
Token based Authentication requires a triparty trust, the three actors are the client, server, and authority. The client acquires a token from the authority, this token is then sent with every request (in place of the password in basic authentication), the server verifies this token with the authority.
There are many advantages of token based authentication, one of the most beneficial is that tokens usually have a validity window meaning that if the token becomes compromised it can only be used during the lifetime of the token, there are also numerous dynamic ways that a token can be secured, I will go into these in another article.
Azure Managed Service Identities Link to heading
In Azure most services offer both basic and token based authentication with token based authentication being referred to as “Managed Service Authentication”, Entra ID (previously Azure Ad) plays the role of the authority.
The following examples show a service (client) communicating with a database (server):
Basic authentication:
using Microsoft.Data.SqlClient;
var connectionString = "Server=mysql.database.windows.net;Database=AwesomeDb;Uid=appUser;Pwd=Password!23;";
var sqlConnection = new SqlConnection(connectionString);
sqlConnection.Open();
// Run DB Operations
Managed Service authentication:
using Azure.Core;
using Azure.Identity;
using Microsoft.Data.SqlClient;
var connectionString = "Server=mysql.database.windows.net;Database=AwesomeDb;";
//Get a credential then a token for the approperiate scope
var tokenCredential = new DefaultAzureCredential();
var token = await tokenCredential.GetTokenAsync(new TokenRequestContext(["https://database.windows.net/.default"]));
//Add the token to the connection
var sqlConnection = new SqlConnection(connectionString);
sqlConnection.AccessToken = token.Token;
sqlConnection.Open();
// Run DB Operations
Azure allows basic authentication to be disabled for a number of services, I would recommend disabling this on all services where possible.
Token Providers Link to heading
Microsoft provide a number of credential providers to assist developers, a few that I find useful are
| Provider | Description |
|---|---|
| Az Cli Credential | This will use the credential that is currently logged into Azure Cli |
| Chained Token Credential | Chained Token Credentials is a very useful tool, it is not a credential provider rather a wrapper around other credential providers. This can be very useful if you want to use one credential for development and another for Production. |
| Default Azure Credential | Default Azure Credential is very similar to Chained Token Credential above, however the providers are pre set, to learn more Click here |
| Environment Credential | Environment Credential is useful when you do not have access to a resource managed by Azure or any of the other authentication methods, this allows client credential information to be set as environmental variables in order to obtain a token, to learn more Click here |
| Managed Identity Credential | This credential is for service on Azure, generally it is the one to use in production when your services are on Azure. |
| Visual Studio Code Credential | This will use the credential that is currently configured in Visual Studio Code. |
| Visual Studio Credential | This will use the credential that is currently configured in Visual Studio.  |
For more information on Azure Identity Credential Providers Click here